8.5.1 Configuration and Compliance Management Process Definition and Components
For effective configuration and compliance management, the following must be in place:
 Configuration and
Configuration and compliance tools to capture the current state of the vCloud environment.
 Automation and
Automation and w
orkflow tools to detect, report, and remediate non-compliant systems.
 A CMDB, CMS, or other corporate data schemas to identify where the single sources of truth exist within a vCloud
A CMDB, CMS, or other corporate data schemas to identify where the single sources of truth exist within a vCloud p
rovider or tenant organization.
 Defined vCloud provider or tenant
Defined vCloud provider or tenant standards and compliance policies.

Defined
vCloud provider or tenant change management policies
for compliance remediation.
 Defined vCloud provider or tenant
Defined vCloud provider or tenant access policies for user access and level of rights.
 Defined vCloud provider or tenant
Defined vCloud provider or tenant network security policies.

Well-understood roles and responsibilities.

Ability to capture, record, and view KPI statistics.
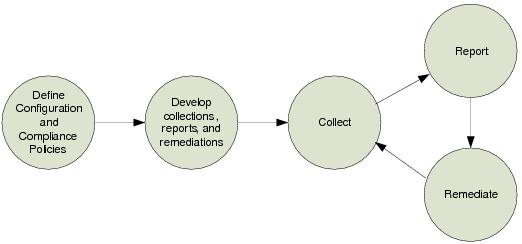
The following figure shows a high-level view of the configuration and compliance management process.
Figure 28. High-Level Configuration and Compliance Management Process
The process involves the following steps:
1. Define the standards and compliance policies. This is an ongoing process that must be updated as new components are developed and compliance policies evolve. Goals must be established for level of compliance and time to remediate.
2. Develop content for the following areas:

Collections to validate compliance

Reports to show levels of compliance

Automations and runbook entries to remediate non-compliance
3. As part of a regular cycle, gather information about the following:

Configuration settings for standardization and hardening

Firmware, software and patch levels

Status and completeness of change records, especially for systems subject to compliance regulations

User access records such as rights allowed, logins, failed logins, commands used, and others

Network access records such as firewall rules, denied access, and so on
4. Evaluate the results and generate reports that show the level of compliance for each area.
5. Remediate if non-compliance is detected. Depending on the type of non-compliance and any impacted service levels, different levels of urgency might apply.