5.11.3 vApp Load Balancing Examples
This section provides examples for each type of load balancer use case.
5.11.3.1. Example: External Hardware-Based Load Balancer Appliance
Third-party hardware load balancers provide options to control exactly how the load is to be balanced or distributed. Load balancers are not restricted to web traffic only—they can often be configured to handle arbitrary protocols. When you have esoteric workloads that you need to put behind a load balancer, these hardware boxes are still the most feature-rich option available.
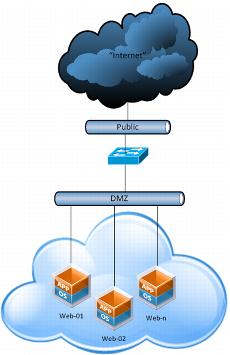
In a vCloud Director environment, the most straightforward way to use hardware load balancers is by putting the back end (load to be balanced) virtual machines on a directly attached organization virtual datacenter network that is shared with the back end connection of the load balancer. This is usually thought of as a DMZ network. The load balancing logic is contained in the load balancer, and the virtual machines based on vCloud Director are used as pure compute resources.
In the following figure, the DMZ network is a vApp or organization virtual datacenter network that is bridged to the external network. The public network can be any physical networking that routes to the client location.
When evaluating the use of hardware based load balancers, weight the higher per-port cost against the availability of multiprotocol support and other advanced load balancing options.
Figure 35. Hardware-Based Load Balancer
5.11.3.2. Example: Third-Party Virtual Appliance as a Load Balancer
There are many third-party virtual load balancers available with varying degrees of multiprotocol support and advanced features. The third-party configuration works with all virtualization-supported networking protocols that the virtual load balancer supports.
When using a virtual appliance as a load balancer, protect the security of the vApp workloads upstream by using a firewall. In this configuration, vCloud Director does not provide security or isolation for the back end workloads other than what the load balancer provides.
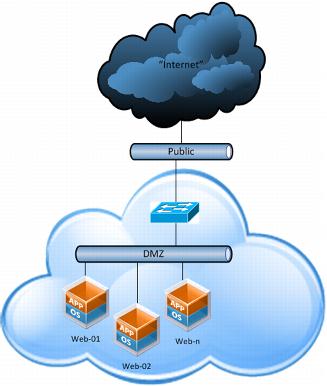
In the following figure, the DMZ network is an isolated vApp or organization virtual datacenter network, and the public network is a vApp or organization virtual datacenter network that is bridged to an external network able to route to clients.
A major advantage in running a virtual appliance instead of a hardware appliance is that the network port can scale up to the bandwidth that is available on the vSphere host (usually 10Gbps per port). In some implementations, having up to 10Gbps of bandwidth available is a significant advantage over the bandwidth available with a physical appliance. Hardware appliances usually are limited to 1Gbps ports.
Figure 36. Third-Party Virtual Load Balancer
5.11.3.3. Example: vCloud Networking and Security Edge as a Load Balancer
vCloud Network and Security Edge offers basic HTTP (port 80) and HTTPS (port 443) load balancing and can be used for applications that need one or both of these protocols. vCloud Networking and Security Edge can be used to load balance vCloud Director cells and the basic web server configuration.
vCloud Networking and Security Edge currently has limited load balancing advanced features such as SSL termination and stickiness. If advanced features are critical to the operation of the application being load balanced, consider evaluating a third-party virtual or physical load balancing appliance.
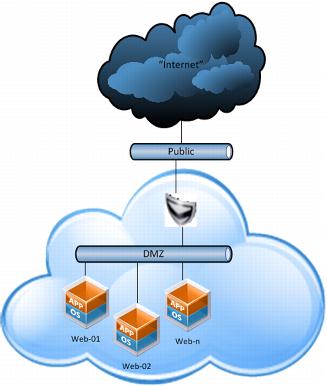
In the following figure, vCloud Networking and Security Edge provides the load balancing functionality and firewall needed to secure the vApp workloads.
As in the third-party virtual appliance as a load balancer example, the DMZ network should be an isolated vApp or organization virtual datacenter network, but the public network should be a vApp or organization virtual datacenter network that is bridged to the external network that routes to client locations.
Figure 37. vCloud Networking and Security Edge as a Load Balancer