VMware vCloud Log Sources for Compliance
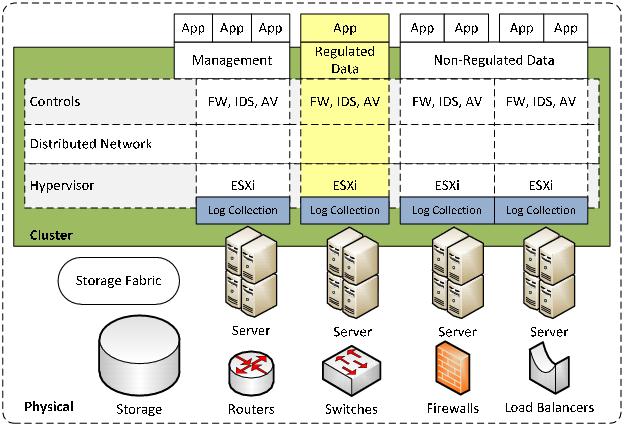
Customers should be able to retrieve logs from all areas that are relevant and unique to their organization. Programmatic retrieval, such as an API to allow for automated queries, should be possible. Log collection nodes must be added to a vCloud environment, as illustrated in the following figure.
Figure 29. Log Collection in the vCloud Environment
Logs generated by VMware components must be maintained by the provider, but also must be available to tenants. Tenants should be able to download in raw format all vCloud Director and vCloud Networking and Security Edge logs that pertain to their organizations and networks. Logs with customer identifiers should be flagged or indexed for retrieval.
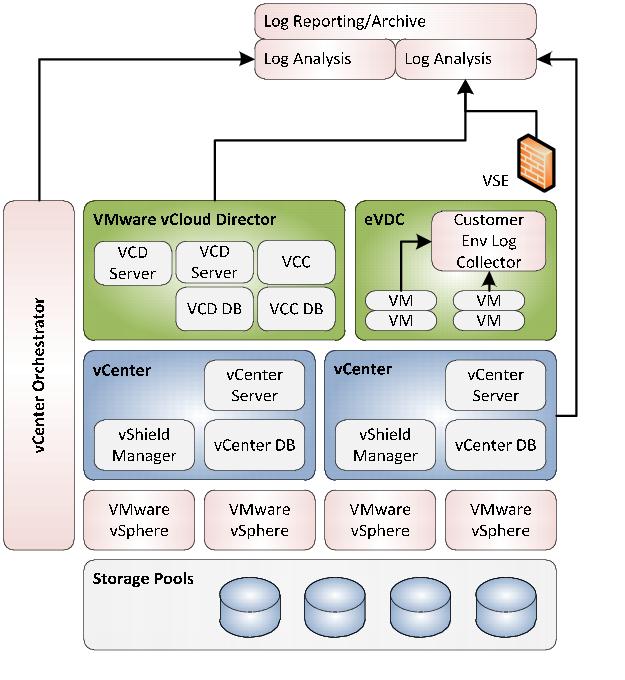
The following figure illustrates architecture of vCloud components and log collection.
Figure 30. Architecture of vCloud Components and Log Collection
The following table lists the logs to which the vCloud tenant must have access.
Table 6. vCloud Component Logs
VMware Component | Provider Logs | Tenant Logs |
VMware vCloud Director | X | X |
vCenter Server | X | |
vSphere Server (ESXi) | | |
Chargeback Manager | X | |
vCenter Orchestrator | X | |
vCloud Networking and Security Manager | X | |
vCloud Networking and Security Edge | X | X |
Other components also generate logs in the vCloud environment that must be maintained by the provider, but direct tenant access is not required.
Table 7. Other Component Logs
Other Component | Provider Logs | Tenant Logs |
vCloud Director DB (Oracle) | X | |
vCenter Database | X | |
vCenter Chargeback Database | X | |
Microsoft SQL Server | X | |
Linux (VCD) | X | |
Windows System Logs (CBM, vCO, vCenter Server) | X | |
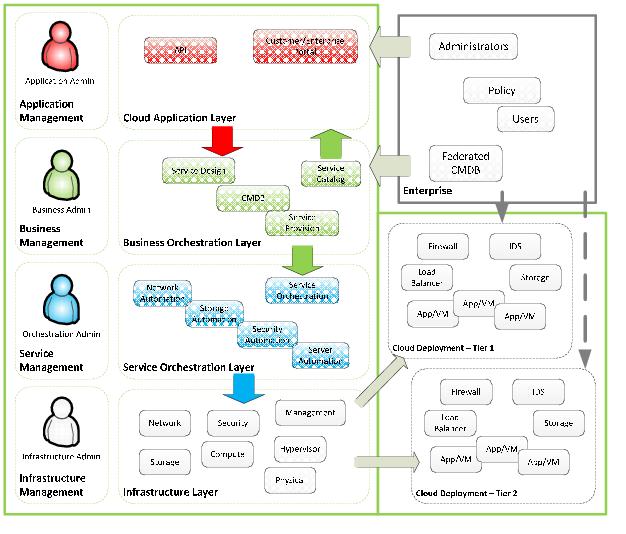
Logs in the vCloud datacenter environment can further be categorized into the following logical business layers:

vCloud Application – Represents the external interface with which the enterprise administrators of the vCloud interact. These administrators are authenticated and authorized at this layer, and have no (direct or indirect) access to the underlying infrastructure. They interact only with the Business Orchestration Layer.

Business Orchestration – Represents both vCloud configuration entities and the governance policies that control the vCloud deployment:

Service catalog – Presents the different service levels available and their configuration elements.

Service design – Represents the service level and specific configuration elements along with any defined policies.

Configuration Management Database (CMDB) – Represents the system of record, which may be federated with an enterprise CMDB.
 Service provision– Represents the final configuration specification.
Service provision– Represents the final configuration specification. 
Service Orchestration – Represents the provisioning logic for the vCloud infrastructure. This layer consists of an orchestration director system, and automation elements for network, storage, security, and server/compute—vCenter Server, VMware vCloud Director (vCloud Director), vCenter Orchestrator.

Infrastructure Layer – Represents the physical and virtual compute, network, storage, hypervisor, security, and management components – vSphere Server (ESXi), vCloud Networking and Security Manager, and vCloud Networking and Security Edge.
Figure 31. Infrastructure Layers
The abstraction of these four layers and their security controls helps illustrate audit and compliance requirements for proper authentication and segregation.
For example, vCloud provider administrator accounts should be maintained in a central repository integrated with two-factor authentication. Different tiers of vCloud deployments (provider virtual datacenters) would be made available to enterprise users.